Technical: macOS X Security – Part 1 – Boot Security
Technical: macOS X Security
Part 1 – Boot Security
 Technical blogs, oh how I loathe thee. While one hand they are fun to research, and I do enjoy delving more and more into the inner workings of macOS X, To me these posts feel the most like actual work. I do not get the enjoyment of taking photographs like I do for travel articles. Or put myself in a well deserved food coma after reviewing a resturant. It’s just mostly research, typing, and the screen shots that go with the article
Technical blogs, oh how I loathe thee. While one hand they are fun to research, and I do enjoy delving more and more into the inner workings of macOS X, To me these posts feel the most like actual work. I do not get the enjoyment of taking photographs like I do for travel articles. Or put myself in a well deserved food coma after reviewing a resturant. It’s just mostly research, typing, and the screen shots that go with the article
They do provide a service to my readers and remain in the top viewed list continuously, so in there in itself is my reward! Now that I have my belly aching out of the way, let’s start a new technical series on Brent’s World, macOS X Security, which will be a multi part blog on keeping your Mac, and your data safe! We will begin with the boot loader, utilities available on the recovery partition and the vulnerabilities they impose and how to protect your system from these vulnerabilities. Subsequent posts will deal with user accounts (Local, and network), file system permissions and access control lists (ACLs), drive and folder encryption, and ending with the sharing options offered with macOS X what they do, and how to lock them down.
So after that long winded preamble, lets dive into the heart of the matter.
Security, security threats, vulnerabilities, hackers, and bad actors. This is something we hear about daily but as Mac users, especially standalone (devices not part of an enterprise environment.) is something we really take no notice of, these happen to other people, people who own PCs. If we do anything at all we install an antivirus package such as Sophos and call it a day! What if I told you there are many more threats out there then just viruses, worms, or ransomware? Those risks raise exponentially if you are a Macbook or Macbook Pro user, simply because if you lose physical control of the device the thief can attempt to gain access at his leisure. “So, my device is password protected!” What if I told you, it is possible to get access to all your data and I don’t even need to enter your password, or that I could change your password from the recovery partition built into your Mac? Let’s take a look at some scenarios, starting from the simple and moving into the more complex.
- The boot loader.

Rebooting or starting a Mac with the option key depressed will invoke the Apple Boot Loader. This will allow me to boot off an external drive such as a thumb drive or external hard drive. Great for troubleshooting, imaging the operating system, or installing the OS if you have completely replaced the system drive. It also opens up your system to several vulnerabilities such as allowing an unauthorized individual the ability to take an image of the system drive, or simply copy the data to an external drive
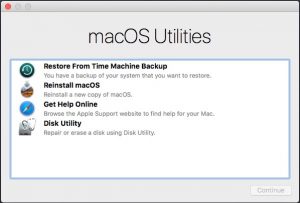
- The recovery partition.
Holding down Command – R after the startup chime will invoke loading the recovery partition, this is a hidden partition that contains a limited, bootable version of mac OS X that will allow you to set an OpenFirmware password (More about this later), access a shell via the terminal.app, Reinstall Mac OS X from a Time Machine backup, Reinstall Mac OS X, and Disk Utility. The recovery partition utilities are very useful when used for their intended purposes, but if left unsecured, by not setting an OpenFirmware password allow several holes into your system. Let me demonstrate.
- Single User Mode (SUM)
Holding down Command – S after the startup chime will place the macOS X computer in “Single User Mode” as the root level account (Even if root is not enabled.). The system volume is loaded as read only, but this can be changed by unmounting and remounting it as read/right. This allows the person who booted the Mac into single user mode full access to any unencrypted data on the drive, the ability to mount removable media to copy this data off the drive. The possibility of installing malicious code, as well as being able to change system preferences from the command line. You may also change any user’s password on the system using Single User Mode.
So we have demonstrated 3 vulnerabilities present at the Mac boot loader, what can be done to harden your computer so bad actors will have a more difficult time exploiting these vulnerabilities? You can set an OpenFirmware password that you will be prompted to anytime you hold down the Command Key during startup. In order to enter the Recovery Partition, or Single User Mode you must enter the OpenFirmware password correctly.
CAUTION: If you lose your OpenFirmware password, you will need to take your Mac to either an authorized service center, or to the Genius Bar at an apple store to have the password cleared. While older Macs (Pre-Intel), did have a reset button on the motherboard. Newer Macs do not. Zapping the PRAM will not clear the OpenFirmware password.
Let me now demonstrate how to set the open firmware password.
NOTE: If you sell your Mac, make sure you either include the OpenFirware password, or clear if before you deliver the Mac to its new owner.
These are the vulnerabilities that exist on your Mac during the boot process, while these might not have much impact if you are using a desktop Mac, it might be something to think about for mobile users.
Thank you for visiting Brent’s World, please come back frequently for more great content. If you wish to be notified by email when new content is posted, please register, by clicking here!

Comments
Technical: macOS X Security – Part 1 – Boot Security — No Comments
HTML tags allowed in your comment: <a href="" title=""> <abbr title=""> <acronym title=""> <b> <blockquote cite=""> <cite> <code> <del datetime=""> <em> <i> <q cite=""> <s> <strike> <strong>